Just adding authentication user identification functionallity on selfhosted webportal based on local active directory
BY NO MEANS SECURE, no input is sanitized…
ref: https://wp.12p.no/2022/05/13/alternative-to-captive-webportal/
First thing that is needed. php-ldap. I noticed it was not supported by php7, so i change php version to 8.x.
# a2dismod php7.x.x
# a2enmod php8.x.x
then
# apt install php-ldap
#service apache2 restart
then created a local website in my apache folder
index.php:
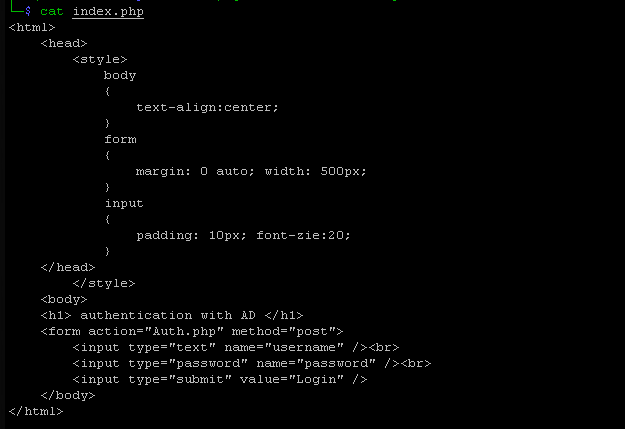
Then create an auth file:
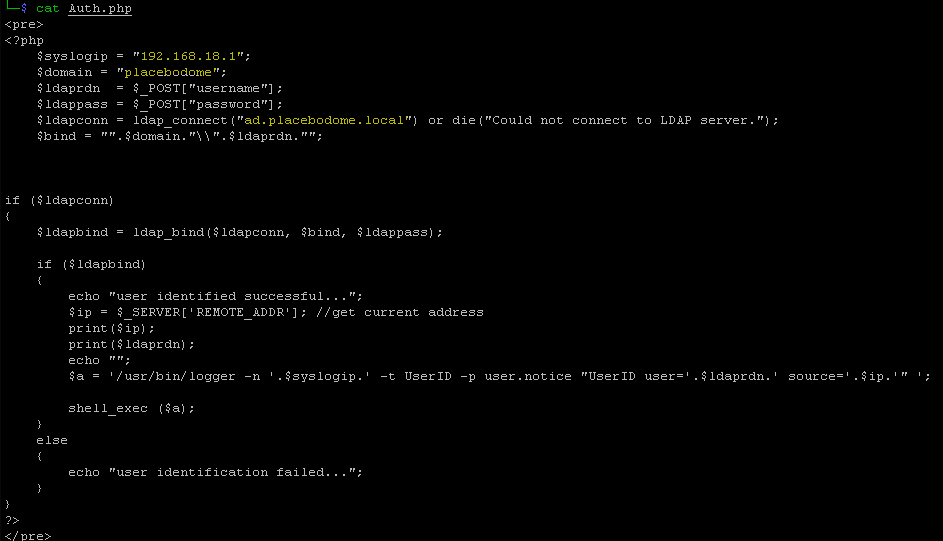
The syslogip points to the syslog recieving interface of paloalto
domain points to the domain name
replace: ad.placebodome.local with your ADs FQDN.
The php-ldap function then tries to bind to the domain using the userprovided username and password. If binding fails the user is not authenticated.
If the binding is successfull a logger command is run to send a syslog message to the Paloalto firewall with username of user and the ipaddress for the requester/user.
As the previouse example: https://wp.12p.no/2022/05/13/alternative-to-captive-webportal/ using the syslog parser:
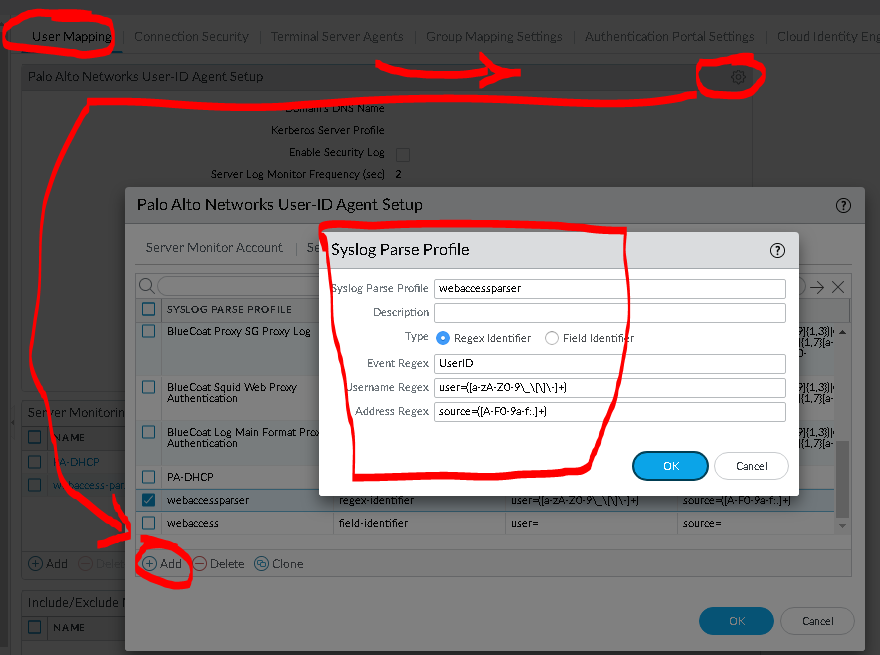
Voila, the user is populated in the same way as the original
Leave a Reply
You must be logged in to post a comment.